-
The End-to-End AI Stack – A Real Guide for Developers to Code, Create, and Execute
Artificial Intelligence tools are on the rise, from writing assistants to coding helpers and automation platforms. However, many professionals struggle to compare these tools effectively. This is where the AI Stack becomes important. Modern AI tools like ChatGPT, NotebookLM, and Antigravity serve different purposes, and understanding their roles helps in:… Read More ⇢
-
10 Workplace Communication Speaking Exercises to Improve Fluency at Work
Strong workplace communication is one of the most valuable professional skills today.Whether you’re giving project updates, speaking to clients, or collaborating with teams — the ability to speak clearly and confidently can set you apart. However, many professionals struggle with: One of the best ways to improve is through chunking… Read More ⇢
-
Step-by-Step: 4 Methods to Create RDS in AWS & Build Schemas
Setting up a Relational Database Service (RDS) database in Amazon Web Services (AWS) is an essential skill for developers and data engineers. This blog post outlines four different methods for creating an RDS database, providing step-by-step instructions that are easy for beginners to follow. Additionally, we will discuss how to… Read More ⇢
-
From Laptop to Cloud: Deploy Your First Production DB Using Amazon RDS
Learn how to move from a local database to a production-ready cloud setup using Amazon RDS. A beginner-friendly step-by-step guide covering setup, backups, scaling, and best practices. Read More ⇢
-
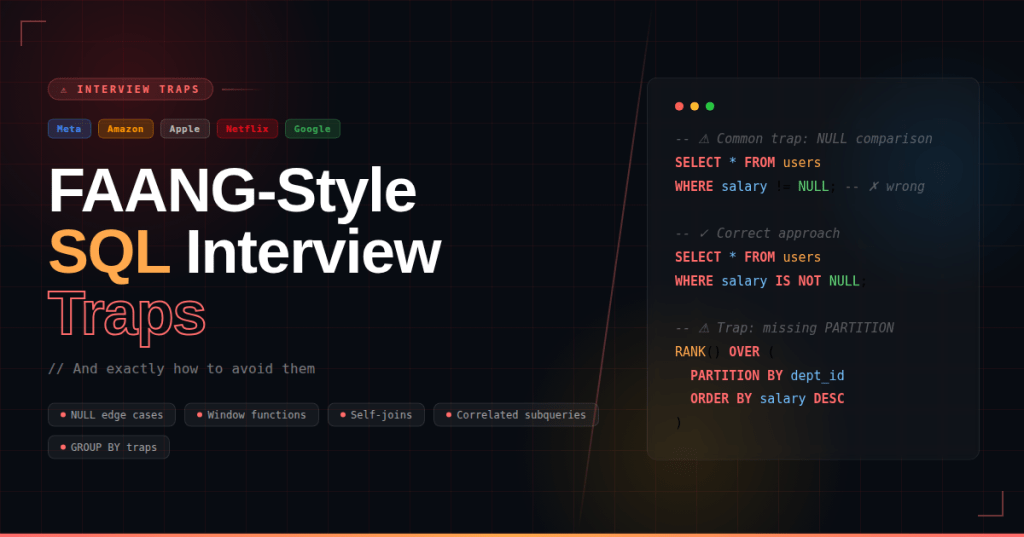
FAANG-Style SQL Interview Traps (And How to Avoid Them)
SQL interviews at FAANG (Facebook/Meta, Amazon, Apple, Netflix, Google) are not about syntax. They are designed to test logical thinking, edge cases, execution order, and data correctness at scale. Many strong candidates fail—not because they don’t know SQL, but because they fall into subtle traps. In this blog, we’ll walk… Read More ⇢
-
Common Databricks Pipeline Errors, How to Fix Them, and Where to Optimize
Introduction Databricks has become a premier platform for data engineering, especially with its robust integration of Apache Spark and Delta Lake. However, even experienced data engineers encounter challenges when building and maintaining pipelines. In this blog post, we’ll explore common Databricks pipeline errors, provide practical fixes, and discuss performance optimization… Read More ⇢
-
AWS Interview Q&A for Beginners (Must Watch!)
The content outlines essential AWS basics interview questions that every beginner should be familiar with. It serves as a resource for fresh candidates preparing for interviews in cloud computing. The link provided leads to additional multimedia content related to the topic. Read More ⇢
-
How a PySpark Job Executes: Understanding Statements, Stages, and Tasks
When you write a few lines of PySpark code, Spark executes a complex distributed workflow behind the scenes. Many data engineers know how to write PySpark, but fewer truly understand how statements become stages, stages become tasks, and tasks run on partitions. This blog demystifies the internal execution model of… Read More ⇢
-
Azure Data Factory (ADF): The Complete Beginner-Friendly Guide (2026 Edition)
Azure Data Factory (ADF) is Microsoft’s fully managed, cloud-based data integration and orchestration service. It helps you collect data from different sources, transform it at scale, and load it into your preferred analytics or storage systems. Whether you are working with Azure SQL, on-premises databases, SaaS applications, or big-data systems,… Read More ⇢